What is a Hash
We often speak in this world of hashes and asymmetric encryption, so it is important to be clear about these concepts that are so widely used in the world of cryptocurrencies.
Hashes
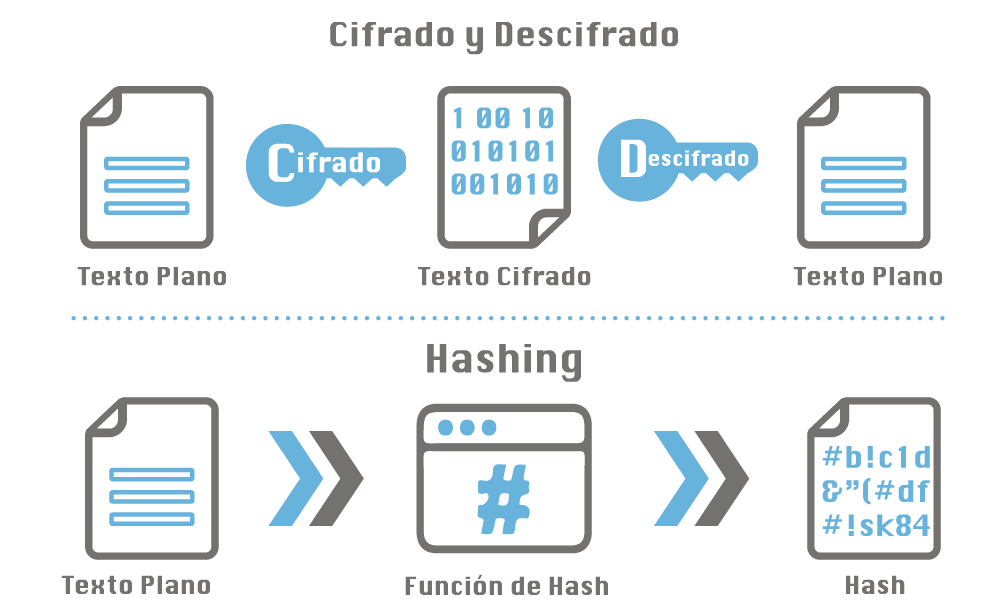
A hash is nothing more than an alphanumeric character set generated from plain text. They are usually finite in length and are characterized by being irreversible and deterministic.
The best known hash function is MD5 and whenever it is applied to a text, the same hash will be obtained, let’s see some examples:
| Text to which apply the MD5 hash function | Resulting Hash |
|---|---|
| hello | 5d41402abc4b2a76b9719d911017c592 |
| hello- | 4f0e5ee00cfa619160879e514d810da5 |
| this is a test creating hashes with md5 | 4faf5356f5b7fe46dd762dd5d5e40e04 |
It can be seen how any change in the original text, no matter how small, generates a totally different result and regardless of the size of the text, the result will always have a length of 32 characters.
When two plain texts have the same hash, it is said that a collision has occurred, however the hashing algorithms ensure that in practice, you will never find two texts that produce the same hash, despite the fact that the results always have 32 characters and the origin can be any possible length.
Obviously this is theoretically impossible, since with only 32 characters, there are a limited number of combinations that can be generated, while the possible texts that can be hashed are infinite, which would imply that there are infinite collisions for each hash. The reality is that the probability of encountering a collision is so insignificant that it is considered totally zero and therefore it is used without fear.
Different cryptocurrencies use different hashing functions, Bitcoin for example uses sha256 which has proven to be quite safe. MD5, on the other hand, is a vulnerable hashing function and should not be used for purposes that require certain security.
A secure hashing function makes it possible to ensure the integrity of the information as a checksum: It is possible to verify that a message and a hash belong to each other as already explained in the solution to Problem of the Byzantine Generals.
Encryption
Encryption or encryption differs from hashing primarily in that it is bidirectional. That is, if you have the private key, it is possible to recover the original data from an encrypted text.
There are different types of encryption:
Symmetric
Use the same key to encrypt and decrypt the message. This key must be known by both the sender and the receiver.
Asymmetric
In asymmetric encryption there are two interrelated keys, one is called * private key * and must be kept secret. The other is the * public key * and it can be published without problems.
Two of the main functionalities that the use of this key pair has is:
- Encryption with Public Key: A message can be encrypted with a public key, and only the owner of the associated private key will be able to decrypt it.
- Digital Signatures: A message is signed using a private key, and all those who receive the public key will be able to verify its authenticity.
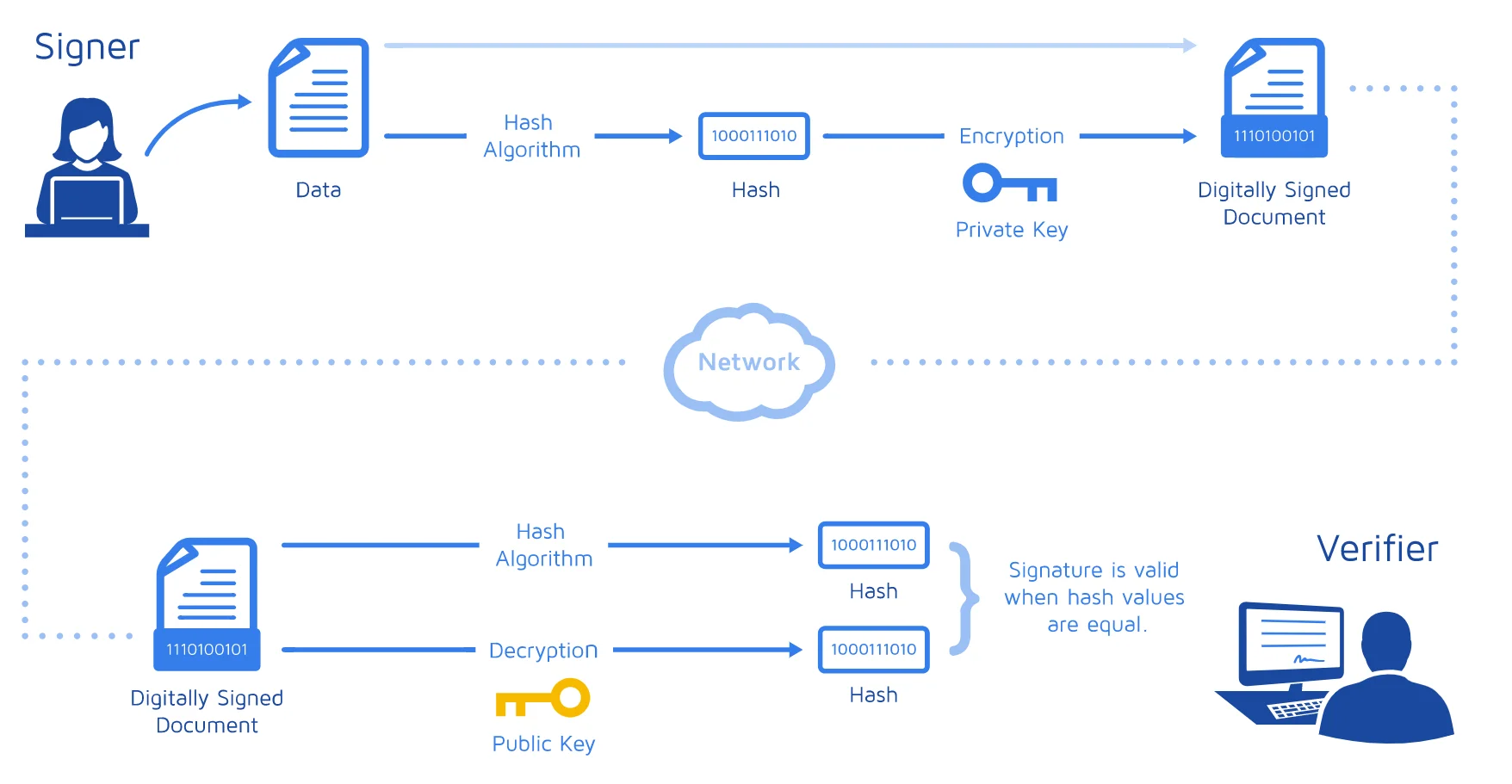
The behavior shown in the image would be:
The issuer is generating the following:
- The document
- A hash of the document, let’s call it A (this can be generated by anyone who has the document since it does not require private/public keys)
- The same hash of the document but encrypted with its private key. Let’s call it B = F (A). This is what is called a digital signature.
The receiver receives:
- The document
- The digital signature B = F (A)
The receiver then generates:
- A hash of the document, which coincides with A, since both the sender and the receiver have taken the same document and have generated a hash with the same formula.
- With the public key, it decrypts the digital signature, making F (B) = A.
If both results match, it can be said that the document and the signature come from the same person who provided the public key to the recipient.

Comments